Risk Management Application – Key to Business Security
Does your company process large amounts of personal data? If so, you certainly know how important effective risk management is. Modern tools automate processes, monitor threats and support informed decision-making, protecting your company from potential threats.
Personal data breaches can result not only in the loss of customer trust, but also in very severe financial penalties. According to the GDPR, this applies to any organization that processes personal data. In the case of NIS2, in particular entities providing postal and courier services, production, transport, energy, finance and ICT services. So how can you protect your company from potential threats and meet all regulatory requirements? A modern risk management application comes to the rescue.
Risk management and GDPR - how to avoid financial penalties?
Today, every company that processes personal data must comply with the strict provisions of the GDPR. Failure to comply with data protection obligations can lead to serious consequences, both legal and financial. Examples from the market show that organizations are severely punished for the lack of a formal risk assessment. This further emphasizes the importance of having solid risk management procedures in your company. Risk management applications help not only to identify risks, but also to avoid financial penalties. Their amount can reach up to 20 million euros or 4% of the company's annual global turnover, depending on which value is higher. Since the GDPR came into force in Poland (25 May 2018), 74 fines have been imposed on Polish companies, totalling over EUR 3.5 million.
The Personal Data Protection Office publishes decisions on imposing penalties on its website, including those related to failure to comply with risk analysis requirements, for example:
- penalty imposed on the Warsaw University of Technology No. DKN.5130.2559.2020 - https://uodo.gov.pl/pl/138/2373.
- penalty imposed on the Mayor of the City and Commune of W. - No. DKN.5131.44.2022 - https://www.uodo.gov.pl/decyzje/DKN.5131.44.2022.
So how can you effectively protect your company and ensure peace of mind?
Agile threat management with a single tool
In the face of the growing number of cyberattacks, organizations must be prepared for every eventuality. Proper risk management not only ensures compliance with applicable legal regulations, but also minimizes potential damage, such as equipment failure or human error. An effective risk management strategy not only protects the company's data and assets, but also strengthens the trust of customers and business partners, which is crucial for maintaining long-term relationships and reputation on the market. Thanks to modern risk management applications, the entire process can be significantly simplified and effective.
The nAxiom risk management application is convenience and functionality
The risk management application was designed to make risk management not only effective, but also convenient. Therefore, the reference point was our many years of practice of cyclical risk analysis in relation to the requirements of the international standard PN-EN ISO/IEC 27001 implemented at OPTeam S.A. In turn, thanks to the intuitive interface, nAxiom allows easy identification and assessment of risks. This is a tool that simplifies everyday processes to the maximum, helping companies to operate faster and more confidently. So what specific functionalities does nAxiom offer to support companies in risk management?
- Definable dictionaries
At the beginning, administrators can freely define dictionaries that will make it easier for participants to analyze concepts "hidden" in individual stages of the process. Thanks to this, it will be possible to adjust the risk assessment to the specificity of the operation of a given organization.
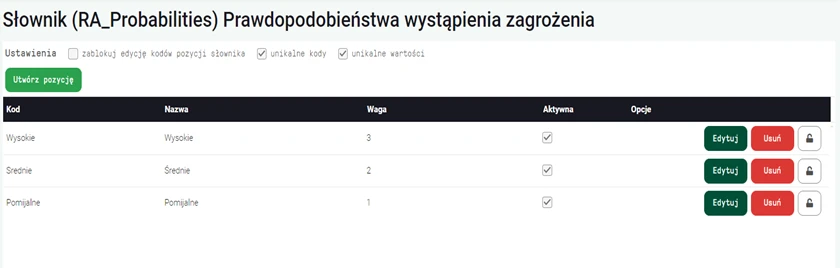 Graphics. 1. Definable dictionaries - probability of threat occurrence.
Graphics. 1. Definable dictionaries - probability of threat occurrence.
Graphics. 2. Definable Dictionaries - Threat Category.
- Configuration of information processing activities
The next step is to define the information processing activities (including internal processes, assets) that will be subject to analysis. The application allows administrators to configure and assign these activities to the appropriate departments in the company. At this stage, it is identified which processes are critical and what data is processed.
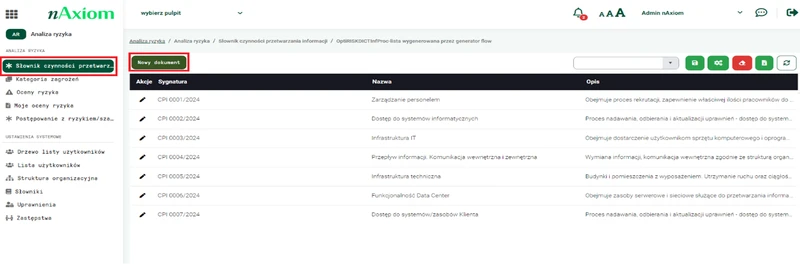 Graphics. 3. Configuration of information processing activities.
Graphics. 3. Configuration of information processing activities.
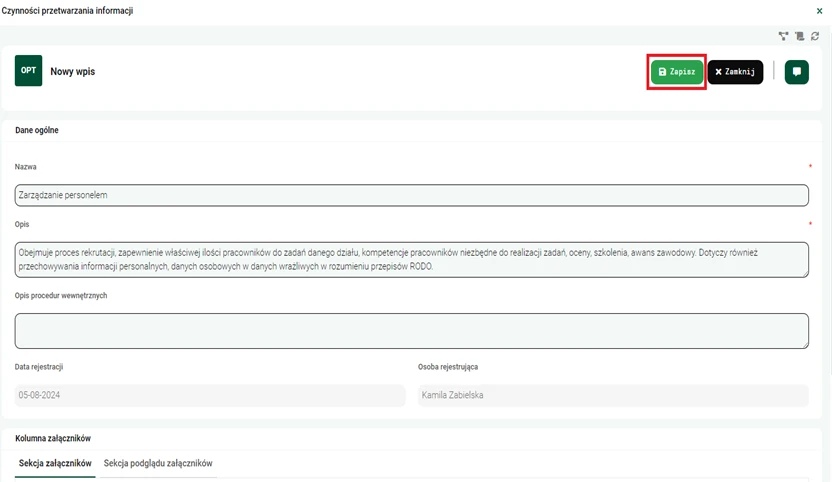 Graphics. 4. Configuration of information processing activities - information processing activities.
Graphics. 4. Configuration of information processing activities - information processing activities.
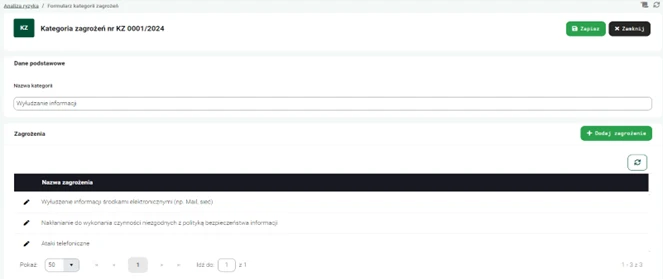
- Creating threat categories
Once processing activities are configured, users of the nAxiom risk management application can assign specific threats to the appropriate information processing activities. Analysis participants can use predefined dictionaries that include different types of threats, such as cyberattacks, hardware failures, human errors, and threats related to physical access to data. Each threat can be classified according to the specifics of the company's business, allowing for more precise monitoring and management of potential risks.
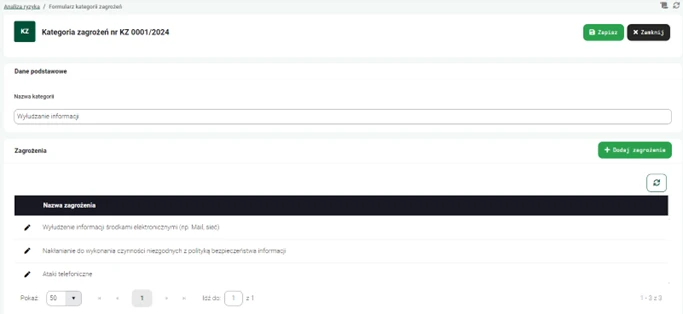 Graphics. 5. Creating threat categories.
Graphics. 5. Creating threat categories.
- Risk assessment
After relating the threat categories to information processing activities, the analysis participants determine the probability of these threats occurring and what effects such events may have on the organization. In this way, entries are created for each department assessing the risk associated with selected information processing activities. Thanks to this, each department can perform a detailed threat assessment. It should be emphasized here that the application is flexible enough to allow risk measurement also in the shade of GDPR requirements in terms of risk to the rights and freedoms of persons whose data the organization processes.
After the analysis is completed, the system automatically changes the status of the main analysis to processing the results. At this stage, the application identifies risk levels and allows drawing conclusions about unacceptable risks, based on which the procedure for dealing with them is developed.
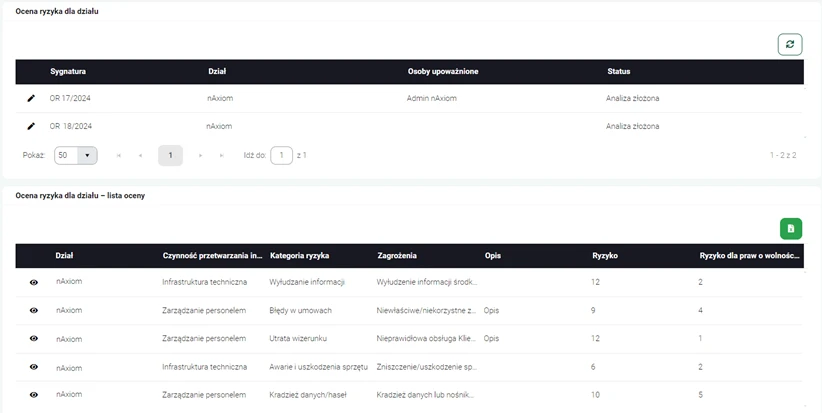 Graphics. 6. Risk assessment..
Graphics. 6. Risk assessment..
- Risk management
The analysis results are the basis for developing a risk management strategy. The nAxiom application documents all preventive and corrective actions taken to minimize identified threats. These processes are described in detail and the actions taken are reported, which allows for tracking progress and ensures transparency in risk management.
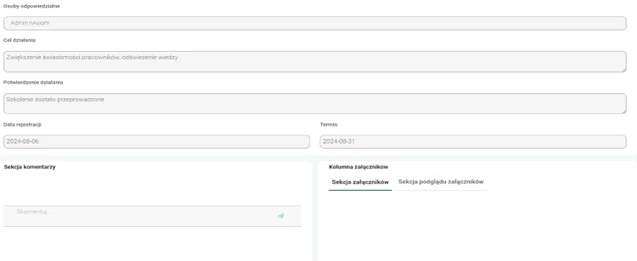 Graphics. 7. Risk management.
Graphics. 7. Risk management.
- Graphical presentation of results
The nAxiom application also offers a module for graphical presentation of risk analysis results, which provides transparency and facilitates the interpretation of risks. Additionally, it is possible to compare the results of two analyses from different periods, which gives an insight into changes in the perception of risks over a period of time.
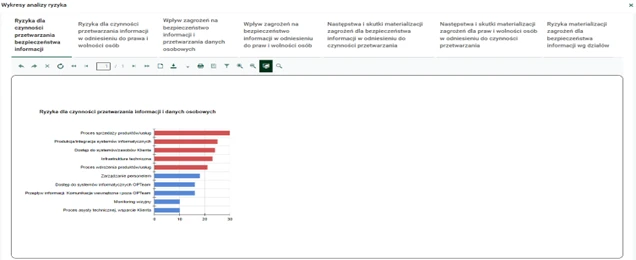
Graphics. 8. Graphical presentation of the results.
Risk management and new regulations, i.e. NIS2 and CER
Risk management becomes even more important in the context of new regulations such as NIS2 and CER. Why? The NIS2 Directive, the provisions of which will enter into force on 17 October 2024, introduces requirements for the implementation of advanced risk management measures in the field of cybersecurity. It will affect many sectors, such as energy, transport, banking, digital infrastructure, health and public administration. Risk management applications such as nAxiom will therefore be a key tool in implementing these requirements, ensuring that organizations effectively identify, assess and minimize risks and comply with new legal regulations.
Tell us your problem and we will suggest how you can solve it.
We take very seriously every question addressed to us. If you tell us what you need, we will discuss together which solutions will best meet your expectations. If you want to learn more about the nAxiom platform, we will tell you and provide you with additional materials. And if you would like to take part in a webinar, we will tell you when the next online meeting will take place and what topics it will cover.
